Introduction
This paper intends to address the communication issue of data breach in companies. StockX is an online store for purchasing and selling clothing items, majorly sneakers. It is based in Detroit and was started in 2015 by Dan Gilbert, Chris Kaufman, Josh Luber, Chris Kaufman, and Greg Schwartz. StockX resells sneakers from several famous brands such as Nike, Jordans, Adidas, and supreme. The company has risen to be one of the best online sneaker shops in the world. It also deals in designer handbags, watches, and streetwear. Managerial communication is about how managers and employees communicate with each other. The purpose of this report is to provide information about a managerial communication issue. It is about the view of a business issue at the stand point of a managerial communication topic.
The Data Breach
In May 2019, StockX suffered a data breach that leads to the leak of customer records of up to a 6.8million customers (Wertheim, 2020). StockX is reported to, however, not have been upfront with revealing this information to its clients. StockX stated that they were made aware of the suspected data security issue on July 26, after which they engaged data security experts in investigating the matter. The investigations concluded that an unknown third party had accessed and stolen customer data (Rosati et al., 2019). StockX sent emails on August 3 to its customers asking them to reset their passwords.
However, the emails stated that the request was due to system updates and did not even explain what caused the system updates. This misinformation raises questions on why StockX did not inform their customers of the data breach. It has caused suspicions that Stock X was trying to cover up the system update. On August 8, StockX made an update on the previous email they had sent to its customers. They gave details on what happened and assured clients that no payment or financial information of clients had been accessed.
TechCrunch later reported that an unidentified data breach seller contacted them and informed them that StockX data was breached earlier in May and details about a 6.8million users exposed (Wertheim, 2020). The data breach seller gave TechCrunch a sample of some user data to confirm the claim. On contacting the customers, the clients confirmed the data provided to TechCrunch. The data comprises information that only the users could know, such as real customer name, shoe size, and username combinations.
The seller stated that the data was being sold on the dark web for 300 dollars (Wertheim, 2020). By the time he was sharing this information with TechCrunch, one person had already bought the data. The stolen data contained details such as customer email addresses, real names, trading currency, scrambled passwords, and the customer’s shoe size. The type of device the customer used, and its software version was also included in the data. The hackers had also accessed information about whether or not the customers had accepted the company’s General Data Protection Regulation (GDPR) message. However, the data breach seller did not state how the data was obtained.
How Stockx Has Handled the Breach
On its updated statement, StockX stated that apart from conducting thorough investigations into the matter, they also made changes to their infrastructure to prevent any possible effects of the security attack; they did a system upgrade and upgraded the encryption of the customer passwords (Yılmaz & Gönen, 2018). StockX also reported the incident to law enforcement, who immediately started their investigations on who the perpetrators might be.
Stock X also stated that to ensure extra protection from future attacks, they would provide their users with one year of free fraud detection. In the 12 months, they would also provide free identity theft protection to clients by providing MyIDCard to them through ID Experts.
The MyIDCard would provide services such as cyber-scan monitoring, ID recovery in case of theft, free credit monitoring for 12 months, and a $1,000,000 insurance reimbursement (Mohamed, 2016). StockX provided guidelines to its clients to protect them from the effects of the Breach. The customers have been advised to promptly check their credit and debit cards and report any unrecognized or suspicious activity. They have also advised their customers to ask for additional account security from their banks of choice. Customers were also urged to change passwords in their other accounts if they were using similar passwords as in the StockX account.
Consequences
Failing to reveal the breaches to the public became a business concern when EU GDPR is involved. According to GDPR, the company should have notified the EU supervisory within 72 hours of becoming aware of the security data issues. An exception to this is if the Breach is not likely to put the rights and freedoms of individuals at risk (Voigt & Von dem Bussche, 2017). Failure to these rules could result in paying a GDRP fine of 2% of total annual turnover. These fines could go up to 4% due to the infringements which might have resulted from the Breach. The Breach has exposed StockX clients to a lot of other security risks. Their details that were exposed can be used in identity theft. There was also a potential of the user information being used to access their other accounts or access their bank details (Chen & Jai, 2019). Some clients have also lost their trust in StockX due to fears of being exposed to fraud.
Data Security
The user passwords of StockX customers have been encrypted with the Message Digest (MD5) algorithm and salts. This hashing algorithm has collision weakness and hence can be easily cracked by attackers successfully. Message Digest algorithm five is generally considered insecure as it has been cryptographically broken (Rachmawati et al., 2018). Salting in data security is a concept where some values are added at the end of the password to develop a different hash value. However, even with salts, Message Digest 5 is still not a secure algorithm. StockX should update its data security systems. They should use more secure hashing algorithms such as SHA-256 and SHA-3. Algorithms such as bcrypt and scrypt are also available for use.
The Class-Action Lawsuit
StockX has also faced a class-action lawsuit over the security breach. The lawsuit was filed in the District of Michigan by a group of victims claiming that StockX failed to protect their personal information and concealed some part of the information about the Breach. The plaintiffs stated that the Breach details were not revealed to them until 13 days after the Breach on August 8 (Manworren et al., 2018). They asked for monetary damages in values that be determined in trial.
In July 2020, StockX vice president of product development Stephen Winn signed a motion filed by the company arguing that the plaintiffs did not have rights to a class-action lawsuit as they signed away this right when they agreed to the terms of service of StockX (Manworren et al., 2018). StockX terms of service state that you can only bring claims against them individually and not as a member of a class. StockX also motioned that the plaintiffs had not asked for their accounts to be deleted despite their concerns. StockX pushed. A Michigan federal judge granted StockX’s motion to compel arbitration.
After the Breach
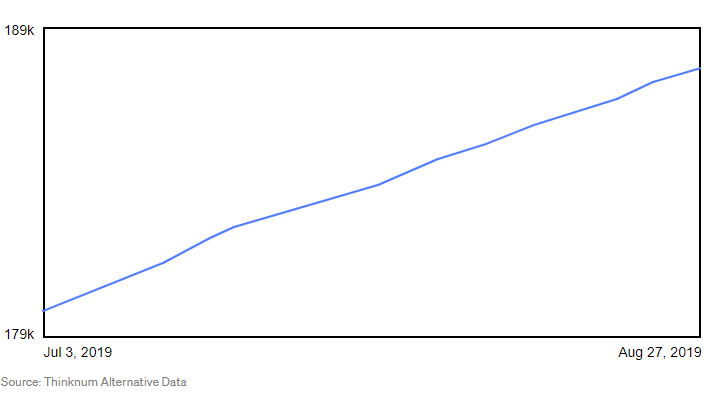
The image above shows the sales trend immediately after the breach. As of January 23, 2020, the online store was booming, with a market estimation of about $2 billion (Manworren et al., 2018). These figures are still rising as the business continues to thrive. This success is also attributed to the fact that there are only a few thriving online stores. StockX has also widened its niche; it is now also selling electronic items, phones, game consoles, and computer hardware.
However, there have also been claims that hackers are using some user accounts to make fraudulent purchases (Manworren, Letwat, & Daily, 2018). Other hackers are also selling their products on StockX at inflated prices. Some of these products are also low quality. These fraudulent acts have to lead to low ratings and bad reviews on the site. Some users also still feel that the company did not make enough effort to help the victims. This perception has caused a bad rep among the company among potential clients.
Conclusion
The Breach of StockX is a clear indication of the importance of securing customer data. Companies, both online and physical, should invest in their security systems to protect user information. Companies should be upfront and reveal all the information about the Breach in case of a security breach. Companies are also urged to take responsibility and protect their clients in case of such security issues. StockX also needs to implement more public relations strategies to recover the trust of its users. The recovery of StockX from the Breach also gives hope to companies that have been victims of breaching to recover from the security breach.
References
Chen, H. S., & Jai, T. M. (2019). Trust fall: Data breach perceptions from loyalty and non-loyalty customers. The Service Industries Journal, 1-17. Web.
Mohamed, K., Sidi, F., Jabar, M. A., & Ishak, I. (2016). Protecting wireless data transmission in mobile application systems using digital watermarking technique. Journal of Theoretical and Applied Information Technology, 83(1), 52.
Manworren, N., Letwat, J., & Daily, O. (2016). Why you should care about the Target data breach. Business Horizons, 59(3), 257-266. Web.
Rachmawati, D., Tarigan, J. T., & Ginting, A. B. C. (2018). A comparative study of Message Digest 5 (MD5) and SHA256 algorithm. In Journal of Physics: Conference Series (Vol. 978, No. 1, p. 012116). IOP Publishing. Web.
Rosati, P., Deeney, P., Cummins, M., Van der Werff, L., & Lynn, T. (2019). Social media and stock price reaction to data breach announcements: Evidence from US listed companies. Research in International Business and Finance, 47, 458-469. Web.
Voigt, P., & Von dem Bussche, A. (2017). The EU general data protection regulation (GDPR). A Practical Guide, 1st Ed., Cham: Springer International Publishing, 10, 3152676. Web.
Wertheim, S. (2020). Tips for Fighting Off Cybercrime in 2020. The CPA Journal, 90(3), 64-66.
Yılmaz, E. N., & Gönen, S. (2018). Attack detection/prevention system against cyber-attack in industrial control systems. Computers & Security, 77, 94-105. Web.