Abstract
Risks are prevalent in all types of economic activities. If appropriate remedial measures are not adopted, these risks could result in substantial losses and render a business organization ineffective. The main aim of this study is to investigate how information systems can benefit the process of risk management. Risk refers to unknown events that can deter the realization of the strategic goals and objectives of an organization. On the other hand, information systems are an array of components arranged in a manner that augments the implementation of strategic goals and objectives of an organization. This research employed a case study approach to investigate the topic at hand. 12 participants were randomly selected from Rolls-Royce Company to shed light on how information systems can benefit the process of risk management. The findings of this study reveal that information systems play an integral in mitigating risks within an organization.
Introduction
Risks are prevalent in all types of economic activities. If appropriate remedial measures are not adopted, these risks (both internal and external) could result in substantial losses and eventually business closure. Currently, risk management is an integral part in many business organizations. This paper investigates the role of information systems in mitigating risks facing Rolls-Royce Company. Risk is defined as “the combination of the probability of an event and its consequences” (IRM 2002). According to the International Federation of Accountants, risk refers to “uncertain future events that could influence the achievement of the organization’s strategic, operational and financial objectives” (IFA, 1999).
According to the Institute of Electrical and Electronics Engineering (IEEE), information system (IS) refers to an array of components that are arranged in a systematic manner to facilitate the implementation of some functions (IEEE, 1990). According to Nickerson (2000), an information system comprises of technical components (i.e. Computers), information, processes, and people. The Committee on National Security Systems (2006) defines an information system as “a set of information resources used to collect and store, process, maintain, use, share, disseminate, dispose, display, and transmit information”. What is more, Wognum et al. (2004) assert that the purpose of an information system is to augment information requirements of firms. There are various types of information systems. They include: Supply Chain Management (SCM) systems, Customer Relationship Management (CRM) systems, Product Data Management (PDM) systems, and Enterprise Resource Planning (ERP) systems (Loh & Koh 2004; McAfee 2002). This dissertation will investigate the implementation of ERP system at Rolls-Royce Company to mitigate strategic and operational risks.
Background
This paper will focus on the process of risk management. All organizations face potential or real risks at one point or another. If left unmitigated, risks can lead to substantial losses or even business closure. Consequently, firms need to embrace information systems that can assist them in the process of handling these risks. Some organizations have scarce resources which limit their abilities to adopt high-tech information systems for risk management.
Prior to looking at ways in which information system is related to risk management, it is necessary to outline the process of risk management. This process entails nine steps. The first step entails the characterization of the system. The second step is the identification of threats. These may be natural threats (i.e. Hurricanes or floods), human threats (i.e. Cyber attacks, data loss, fire, physical weapons), and environmental threats (i.e. Water damage, pollution or power failure). The third step entails identifying the vulnerability identification. This step relates to all the potential flaws that may lead to the manifestation of a potential threat. The fourth step involves carrying out control analysis. The analysis entails analyzing threats and vulnerabilities. The fifth step entails performing a likelihood determination. This is usually computed through percentages. One must quantify the possibility of the manifestation of a threat against the vulnerability associated with it. As a sixth step, the business must carry out an impact analysis of the threat. A threat may have a negative impact on the capabilities of an organization. It may lead to financial losses or the loss of human life. The seventh step is the actual risk determination phase. This entails the impact of a threat as measured against vulnerability. Risk determination precedes control analysis which may range from mitigation, acceptance, transference, and avoidance. Finally, the ninth step entails the documentation of the results of the findings.
After analysis of what is involved in the risk management process, it is necessary to look at how this relates to information systems. Most literature on information systems and risk management tend to focus on how risk management affects information systems. Sample cases include Birch and McEvoy (1992), Wiseman (1992) and the Audit Commission (1990). While the approach is useful, it is not the point of focus for this paper. On the contrary, this paper will focus on the role of information systems in the process of risk management. Some scholars have attempted to look into this subject but most of them tend to dwell on organizations such as finance or insurance firms. Examples of such studies include Gibson (1997), Picoult (1996) and Lawrence (1995). This is nonetheless, too narrow to be applied to other firms in non-financial sectors such as retail, manufacturing or food.
Consequently, it is necessary to expand the application of information systems in risk management to a wider range of organizations. Some studies have also focused on the importance of information systems in risk management. However, most of them are principally descriptive. A typical example was a research carried out by SANS (2006). The company focused on general applications and IS tools used to improve risk management. Whereas broad discussions were made about the relationship between these two terminologies, the relevant examples were missing in this paper. This research will attempt to fill all the mentioned gaps. First, it will focus on the impact of information system on risk management and not vice versa. Second, it will cover an organization that does not fall in the financial sector so that other companies can relate to it. Finally, the paper will not focus on common generalizations about the matter. Instead, it will look at the successful application of IS in risk management at a chosen organization.
Statement of the Problem
Risk is part and parcel in every business activity. Consequently, each firm must learn how to handle risks subject to the characteristics and size of its operation. This is because poor management of risks can lead to business closure. What is more, business organizations are currently experiencing greater risks compared to the past because the interrelationships between the legal, technological and economical aspects are highly prominent and rife. It would be presumed that the type of information system (IS) adopted to manage risks depend on the size of the firm as well as the industry sector. Consequently, this paper assumes that each firm has adopted a robust information system and risk management strategy to accomplish strategic goals.
Risks may negatively affect various organizational activities such as technology, finance and strategic operations of a firm. To be precise, risks may result in ruthless interruption of information flow, considerable decline in financial assets and other physical adversities. What is more, mismanagement and fraud qualify as risks inherent within the organization. It is against this backdrop that this paper will investigate the role of information systems in mitigating risks facing Rolls-Royce Company.
Statement of Hypothesis
The main hypothesis of this paper is:
To determine how information systems benefit the process of risk management in a real organization.
The minor objectives that will be covered in this study are:
- To determine how information systems boost risk assessment.
- To analyze how information systems enhance the effectiveness of risk control.
Scope of the Study
This dissertation is limited to the study of the Rolls-Royce Company found in the United States. The study will mainly focus on the administration department, IT department, human resource department and accounts department. The rationale for selecting these departments is that they are mainly responsible for managing risks that affect the organization.
Structure of the Dissertation
This dissertation is structured into six chapters. Chapter one provides the introduction to the study. Chapter two provides a literature review pertaining to the topic under investigation. Chapter three discusses the methodology used for this study. Chapter four examines the case study. Chapter four presents data analysis, discussion and interpretation of the findings. Chapter six gives the major findings, recommendations, suggestions, recommendation for further research, and conclusion.
Literature Review
Introduction
This chapter serves the purpose of presenting theories and empirical findings on information systems and how they improve risk management in a real organization. In this chapter the study presents the literature which has been published by accredited scholars on risk management information systems. This section provides a handy guide to the reader by giving explanations concerning the theories made in the area of study in order to form a solid background to understanding this research.
Nowadays, organizations are faced with numerous challenges and hurdles than ever before given the advancement in technology, economic crises and legal complications. As a result, risks may go unnoticed for a long period of time or initial signs ignored by those concerned. Therefore, it is very important for businesses to put in place risk management systems that would help the organization to move forward uninterrupted. For that reason, the study will explore risk management processes and the role played by information systems in these processes. The study will further examine how information systems boosts risk assessment and how the effectiveness of risk controls are enhanced through information systems.
The sources of the literature will be books on risk management and information system. Journals on the subject matter will also be useful in getting direct information related to the role of information system in risk management. Government and other reports will also be useful. In addition, the study will also explore websites and other internet sources to acquire more information on a given company or organization.
Definitions of Risk Management
Andrews and Moss (2002, p. 3) define risks as a probable situation that entail undesired event or occurrence. The coherent process of identifying, appraising and minimising risks is what is commonly known as Risk Management (Andrews & Moss 2002, p. 4). Conventionally individuals are bound to worry and for a very long period of time management of risks were considered to be beyond human beings. However, several forms of risk management, for instance, insurances have been practiced for many centuries.
The most ancient account of insurance (marine insurance) dates back to the 18th century. Farmers formed cooperative societies to protect their produce against the unpredictable elements of weather. Toward the late 15th century, a bank in Italy by the name Monte Dei Paschi was created to act as a mediator for such arrangements. The most famous insurance market was Edward’s coffee house in England, which started operation in 1967 (Figlewski & Levich, 2002, p. 2). Marine insurance gained momentum and in a little while started providing insurance cover against almost all types of risks. From the mid 1600s and 1700s, the idea of probability and its chief properties, the building blocks for risk management, were developed (Figlewski & Levich, 2002, p. 3).
Risk management is an integral part of strategic management in organizations. Haimes (1998, p. 5) defines risk management a process through which businesses procedurally handle undesired events or occurrences related to their activities with the aim of benefiting each activity across its portfolios. Risk management enhances the understanding of probable causes of risks and their impact on the organization. Therefore, risk management enhances the ability of a business to succeed and to minimise distress and uncertainty in attaining its goals and objectives (Haimes, 1998, p. 6).
Risk management is a continuous and progressive process integrated in the organization’s strategies. Risk management addresses scientifically all risks that have impacted business activities in the past, at the present and probably in the future. Risk management is also incorporated in the organization’s culture especially when efficient policies and programs are in place (Klinke & Renn, 2002, p. 1072). According to Jorion (2001, p. 45), risk management translates business strategies into goals and objectives and develops risk-averse staff. For that mater, risk management support emphasizes performance assessment leading to organizational efficiency.
Haimes (1998, p. 7) states that risk management is the foundation stone of good corporate governance. Therefore, risk management enhances service delivery and efficiency in the use of limited resources. Risk management in this case involves identifying, analysing and managing risks that are threatening business resources, assets, employees, and the general input and output. Jorion (2001, p. 47) emphasizes that risk management shields and adds value to the business and its shareholders by supporting its objectives.
Risk management achieves business objectives through a number of ways. First, it offers a framework through which business activities take place in a steady and controlled way. Second, risk management improves the decision making process, planning and prioritizing through an all-inclusive and structural understanding of business activities (Jorion, 2001, p. 47). Third, risk management contributes to more efficient utilization and allocation of the scarce resources within the business. Fourth, risk management minimises volatility in the dispensable activities. Fifth, risk management protects and enhance assets and image of the business. Lastly, it develops and supports individual and organization’s knowledge base (Jorion, 2001, p. 47).
Risk Management Strategies
Traditionally, information systems development was basically meant to avert or minimize system changes. However, nowadays information systems can identify changes as early as possible and initiate early warning for necessary steps to be taken. It entails proactive risk management (Chorafas 2008, p. 9). The most common risk aversion techniques include archetype and surveying where those responsible try out different risk aversion alternatives on an impromptu basis (Boehm, 1991, p. 33). According to Boehm (1991, p. 34), archetype and progressive development are generally used to avert risks. They entail knowledge development, dividing the project into subgroups, and minimization of specification time and risk impact.
The risk aversion techniques were then followed by new approaches; the most dominant of them all are the agile techniques. Some of the most notable agile techniques include Extreme Programming (XP), the Dynamic Systems Development Method (DSDM), Scrum, Crystal, Feature Driven Design (FDD), and Lean Software Development (LSD) (Stapleton, 1997, p. 4). All of these are risk management information systems (Hall, 1998, p. 3). The risk management information systems are primarily used by the organizations to respond to the rapid changes in the business environment and in risk management. Some literature has associated rapid changes in the business environment with risk prevalence in most companies (DeMarco & Lister, 2003, p. 100)
The current risk management information systems work by regulating the time and resources to accomplish business objectives and to minimize risky incidents. The developers of these systems kept in mind that each organization is unique in every aspect and therefore requires customized systems. For this reason, the information system used in each company is tailored to their needs (Reifer, 2002, p. 17). Dynamic Systems Development Method (DSDM) components include operational archetype iteration, followed by actual project implementation, identification of iteration stage, consensus, conception and re-evaluation of archetype. The DSDM principles are based on risk management processes. These processes are suitable risk list, risk identification, risk log-update, risk monitoring, risk alert, and risk assessment (Hall, 1998, p. 3; Stapleton, 1997, p. 6).
According to Beynon-Davies and Williams (2003, p. 29), regardless of the risk management information system used risk management process must be adhered to. Risk management has gained popularity among the business community given the turbulent business environment and increased cases of project failures. Therefore, risk management procedures are being observed zealously by organizations today. Over the recent past, organizations and institutions have placed more emphasis on the significance of integrated risk management. Integrated risk management is also known as consolidated risk management or enterprise-wide risk management (Beasley, Clune & Hermanson, 2005, p. 563).
Integrated risk management entails risk assessment and management of a company-wide basis. Interest in integrated risk management has tremendously grown for a number of reasons. The most important of them all is the development in information communication technology (risk management information systems) which has made it possible to quantify risks more accurately (Figlewski & Levich, 2002, p. 12). Integrated risk management has two important facets: synchronized assessment and management of risks across diverse classes of risks and consolidated risk evaluation across all units or branches of the company. Theoretically, the two dimensions are very important to achieve the total evaluation of risk (Figlewski & Levich, 2002, p. 13).
Most organizations generally develop risk management strategies as part of their risk management process. Risk management strategies are aimed at assessing risks, responding to risks and monitoring risks, thus plays a major role in making operational and investment decisions. Risk management strategies are also part of the risk response strategies. The turbulent environment facing the business today necessitates risk response strategies (Braithwaite & Drahos 2000, p. 18).
Risk management strategies entail risk aversion, risk diminution, spreading of risks and transferring of risks to other businesses (Chen, et al. 2008, p. 39). Risk evasion simply refers to policies and strategies put in place to avert risks associated with certain responsibilities, activities, or projects within and without the organization (Chen, et al. 2008, p. 41. Risk avoidance is normally a business decision and is an excellent strategy especially when the business environment is imprecise, ambiguous or deficient (Chen, et al. 2008, p. 42).
Risk diminution is the process of amalgamating risk responses or controlling losses to abate risks. Risk reduction strategy serves to abate the possibility of incurring losses and minimising the frequency or severity of the risk. This strategy works best in collaboration with other risk management strategies because using risk abatement strategy alone cannot achieve the objective of risk elimination (Chen, et al. 2008, p. 41).
Risk preservation is also an excellent risk management strategy especially when risk transfer is not possible. This strategy is also convenient when economic appraisal of organization’s losses establishes that the miniature value placed on the risk can be absorbed. Another case where this strategy is applicable is when the losses are too high such that risk transfer would cost more than the worst risk that can ever occur (Nacco & Stulz 2006, p. 9). In a nutshell, the strategy is used when the probability of the loss is high that it is best to retain the risk than to transfer the risk. Risk transfer entails conveying the risk burden from one party to the other. Risk relocation can be done in a number of ways but the most conventional method used is insurance and contract indemnification. Lastly, risk allocation involves sharing or apportioning of risks among different parties. This is common especially in cases where the cost of risk is too high to be incurred just by one party (Nacco & Stulz 2006, p. 9; Braithwaite & Drahos 2000, p. 18).
Risks facing businesses and their activities can be caused by internal and external factors. These risk factors are further broken down into strategic risks, financial risks, operational risks, hazard risks among others. Financial and strategic risks are internally driven. Financial risks include interests, foreign exchange and credit. On the other hand, strategic risks include competition, consumer dynamics, industrial dynamics, and consumer demands. Operational risks and hazard risks are internally driven. Operational risks include accounting controls, information systems, recruitment, supply chain, regulations, corporate culture, and board composition among others. Hazard risks include employees, public access, product and services, natural events, contracts, and environment (Nacco & Stulz 2006, p. 11).
The decision making processes in most companies can be categorized as strategic, operational, financial, knowledge management and compliance (Nacco & Stulz 2006, p. 11). Strategic activities and decisions are concerned with the long term objectives of the organization, therefore are prone to political risks, legal and regulatory changes, physical environment and capital finance. Operational risks are concerned with the day to day problems that the company is confronted with in achieving its strategic objectives (Nacco & Stulz 2006, p. 12).
Financial decisions touch on the effective and efficient management and direction of the business This is affected by external factors such as credit availability, interest rates, and foreign exchange rates among others (Beasley, Clune & Hermanson 2005, p. 564). Knowledge management is concerned with the efficient management and direction of intellectual resources, production, security and communication. This is affected by both internal and external factors. External factors include competitive technology, abuse of intellectual property, power failures, oil shortage, and civil strike among others. Lastly, compliance is concerned with health and safety, environmental issues, trading, and staff practices and regulations (Beasley, Clune & Hermanson, 2005, p. 565).
Even though many organizations are thought to be autonomous, their operations are imperceptibly controlled by the potential stakeholders and investors. The occurrence insinuates that the organization executives are required by these categories of people to withhold a high degree of integrity and performance (Braithwaite & Drahos 2000). This is very significant in ensuring that the possible projected risks and uncertainties are appropriately managed, and hence crowning the internal and external functions of corporate governance in a business (Nacco & Stulz 2006, p. 11).
Factors that Influence Risk Management
Risk and Culture
The culture of an organization is increasingly being identified as a major factor that influences the success or failure of an organization. Organizational culture comprises of a set of shared values, beliefs, suppositions, and symbols. Organization’s cultures have some predetermined functions and is epitomised by the structure of the organization. The main function of an organization’s culture is to support proper and rational management systems. However, organization’s culture can be influenced to serve corporate interest (Nacco & Stulz, 2006, p. 11). There exist some of the best corporate cultures that organizations should strive for, thus managers should determine the best culture and use them to make changes within an organization. Functionalist view of culture suits risk management for it makes it possible to identify the cause-effects of relationships within an organization (Chen et al., 2008, p. 54).
Management Attitude
The attitude of the managers also influences the level of risks within an organization. For instance, different managers would act distinctively on a certain level of risks to attain a given level of return. The most researched and developed measurement of risks originates from financial/ economic surrounding. Therefore, the risks are appraised by the potential level of loss or gain and the variability around a specific outcome (Kunreuther, 2002, p. 658).
Risk Cognition
Risk cognition refers to how risks are considered from the people’s perception viewpoint. This influences very much on the level of risk incurred (Chen et al., 2008, p. 56). There are two major aspects of risks that influence the people’s perception and that are fear and control.
Personality
Individual’s risk averseness depends partly on the individual’s personality and individuals experience as represented by the pattern of memories, emotions and other cognitive elements and their present situation (Nacco & Stulz 2006, p. 13).
Risk Management Process
Risk management processes include risk analysis (which include risk identification, risk description and risk estimation), risk evaluation, risk reporting (reporting threats and opportunities), decision making, risk treatment, residual risk reporting, and monitoring (The Institute of Risk Management, 2002, p. 16). Both figures 1 and 2 illustrate the processes of risk management that are widely adopted by various organizations.
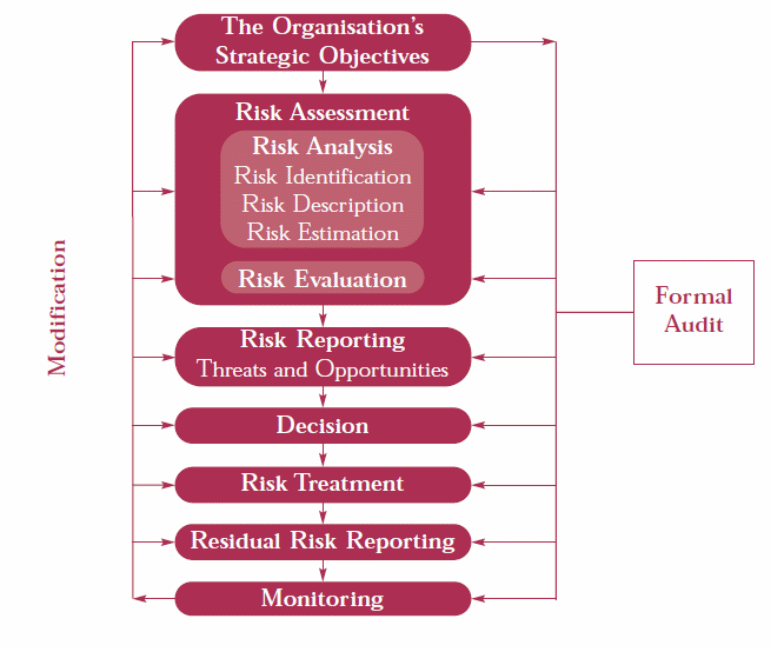
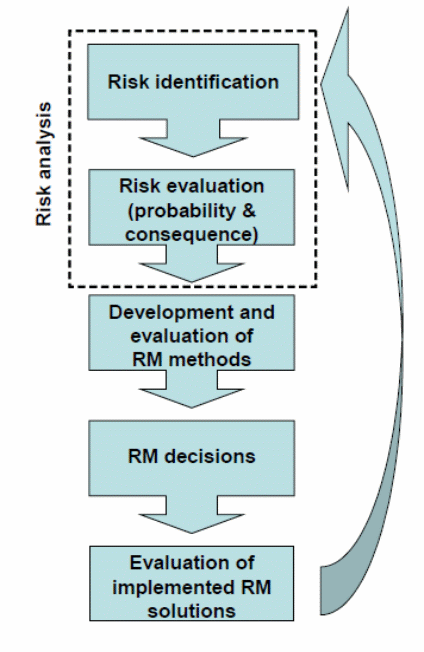
Risks Analysis
Risk Identification
Risk identification focuses on identifying organization’s exposure to risk and uncertainty. Risk identification demands extensive knowledge of the organization, its market, legal, socio-political, and traditional background. Risk identification also requires better understanding of the organization’s strategic and operational objectives including significant factors that contribute to the success of the organization, threats and opportunities (Melnikov, 2004, p. 5).
Risk identification is done systematically to ensure coverage of all the vital activities within the organization and identification of risks attached to these activities. Risk identification entails both top –down and bottom-up approach (Beasley et al., 2005, p. 524). This involves engagement of the management at all levels of the organization to identify, evaluate, and arrange risks in orders. The main aim of these approaches is to identify strategic risks, risks threatening the organization’s strategic objectives and the risks that can be managed at company level. The process of risk identification in any organization helps the management to decide on risks to be managed at different levels. Bottom-up approach to risk management allows the entire organization to make a contribution on efficient risk management practices (Melnikov, 2004, p. 5).
The most significant element of risk identification is classified risks. According to Williams and Walker (1997, p. 76), depending on the size and complexity of the company there are about fifteen classes of risks. Classification of risks normally helps the company to establish different groups that can be solved together (Smith & Merritt, 2002, p. 5). Chapman (1998, p. 335) came up with the two most predominant ways of classifying risks. The first group is classifying risks according to the functions. The functional categories included marketing, finance, and technology among others. For instance, Hillson (2001, p. 22) argues that market risks are heavily influenced by the consumer – acceptability of goods.
The second group is classifying risks as internal or external. This classification provides a wider view of the risk identification process (Chapman, 1998, p. 336). There are numerous sources of risks and these include top hierarchy, consumers, project team, project management, laws and standards, and acts of nature among others (Chapman & Ward, 1997, p. 45). The principal sources of internal risks recognized my many authors include top hierarchy, project organization, and project team and management. On the other hand, the principle sources of external risks include acts of nature, consumers, and laws and regulations (Chapman & Ward, 1997, p. 46).
Each and every source of risks has a number of risk elements. These risk elements are a serious threat to the execution and completion of any project. Some of the risk elements conflict among the project team and budgetary constraints which can be linked to project team and project organization (Chapman & Ward, 1997, p. 46). There are very many risk factors out there and it is very difficult for one study to cover them all (Grey, 1995, p. 7). The link between risk source and risk factors is obvious, for instance, conflict among the team members and project team.
Another dominant feature among some scholars over the recent past is the fact that the sources of risks can also provide an opportunity. Chapman and Ward (1997, p. 46) stresses that once the risk is viewed as favourable companies start to search for opportunities. Very few people will agree that opportunity can also be an element of risk given that the risks are generally associated with negative undertones (Wiegers, 1998, p. 39). Chapman and Ward (2002, p. 13) state that the decision to include both opportunities and threats when defining risks has influenced the success of many projects since they help the project team to act proactively. Therefore, companies and individuals are urged to take risks so as to benefit from the probable opportunities. According to Stulz (1996, p. 9), taking risk is an overwhelming task but advices against undertaking projects with no risks.
Risk Estimation
At this stage potential risks have been identified and are estimated. Risk estimation entails minimization of uncertainty measurements where system variables are described, and the magnitude and impact of the risks is determined (Maurer, 2008, p. 30). Risk estimation also involves an attempt to guesstimate the probability of the incident and exposure to risk (Porthin, 2004, p. 4). Hall (1998, p. 5) defines risk estimation as an assessment of risk probability and its impact. Conventionally, probability is always between zero and one and the risk consequences are measured in terms of cost, deviation from plan and achievement of goals. The probability of one signifies that an event is highly likely or certain to take place (Hall, 1998, p. 6). According to Klinke and Renn (2002, p. 1079), companies should always use probability data to estimate risks. In case there are no probabilistic data, team members of a particular project (especially the most experienced team members) can provide estimates.
Andrews and Moss (2002, p. 56) state that the impact of risk factor can be addressed through qualitative and quantitative analysis. Qualitative analysis entails risk description using subjective units, for instance, decisive, high or low risks. On the other hand, quantitative analysis involves the use of numerical units. Other literatures define qualitative analysis as subjective risk estimation while quantitative analysis is defined as objective risk estimation (Haimes, 1998, p. 6). According to Melnikov (2004), qualitative approaches are personal evaluations that are based on personal opinions. On the other hand, quantitative approaches are objective evaluations that lend credence to statistical methods.
Risk Description
Risk description involves the use of structured format and visual aid to describe risk, for instance, use of charts, tables or diagrams. The tables, charts or diagrams are used to aid the description and evaluation of risk. They are also vital for comprehensive identification, illustration and appraisal of risks. By taking into consideration the impact and frequency of each risk as shown in the formats above, the company would be able to prioritize the intervention mechanism for major risks. Risk description mostly associated with business operations and decision making process can be classified as strategic risks and operational risks (Smith & Merritt, 2002, p. 6).
Risk Estimation
Risk estimation depends on the likelihood of risk occurrence and its probable impact. As a result of the two factors, risk estimation can be classified as quantitative estimation, semi-quantitative estimate and qualitative estimates (Haimes, 1998, p. 4). In terms of the impact risks may be classified as high, medium or low risks. High risks normally exceed the top most thresholds set by the company and can have a devastating impact on the organization’s strategy and operations. Stakeholders may be significantly concerned in case of such occurrences. On the other hand, medium risks like the name suggest normally having a moderate impact on the organizations strategies and operations. They do not attract high level of attention. Lastly, low risk have less impact on the organization in general and in many occasions are ignored. The consequences of such risks are both in terms of threats (normally known as downside risks) or opportunities (commonly referred to as upside risks) (Porthin, 2004, p. 2).
Similarly, depending on the likelihood of occurrence (probability) risks may also be classified as high, medium or low but are defined differently in terms of threats and opportunities. In terms of threats, high probability risks have more than 25 percent chance of taking place or can take place in less than a year. They may have taken place a number of times with a specific period or occurred recently (Andrews & Moss, 2002, p. 53). Medium probability risks have less than 25 percent chance of occurring and could take place more than once with a specified period. These types of risks are normally hard to control because of external influence. Low probability risks in terms of threats are very unlikely to occur and have less than 2 percent chance of occurrence (Andrews & Moss, 2002, p. 54).
In terms of opportunities, high probability risks have more than 75 percent chances of taking place or their positive outcome can be realised in less than a year. They can be relied on with even-handed certainty and are achievable on a short term basis (in less than a year). Medium probability risks in this case have between 25 to 75 percent chance of taking place and can also be achieved in short term depending on the current management process. However, they require cautious management (Andrews & Moss, 2002, p. 54). Last but not least, low probability risks in terms of opportunities have less than 25 percent chance of taking place. They also have chance of positive results in the medium term. Nonetheless, their favourable outcomes are less likely given the available resources. The possible opportunities of these kinds of risks are yet to be explored (Andrews & Moss, 2002, p. 55).
Organizations normally have different measures of impact and probability of risks. For instance, many organizations have found out that measuring the impact and probability of risks using the above criteria (that is high, medium and low risks) is sufficient for their requirement. They normally present it as a three by three matrix. However, some organizations normally apply a 5 by 5 matrix which include all aspects of measurements to achieve better results (The Institute of Risk Management, 2002, p. 11).
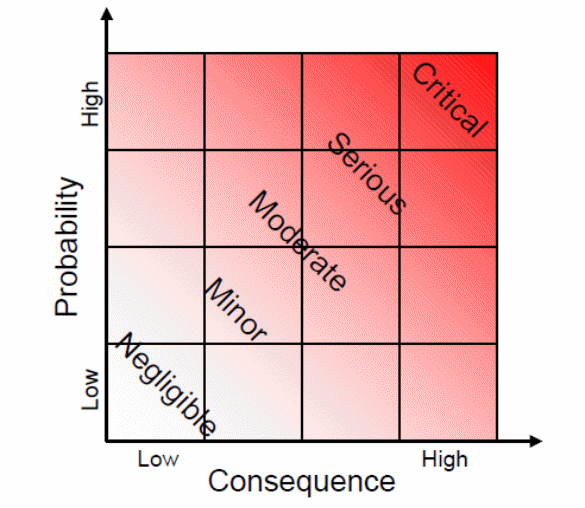
Risk Evaluation
Risk evaluation is the process of comparing the estimated risks against the risk criteria used by the organization. The risk criteria may be based on the costs, benefits, social, economic and ecological factors, stakeholder concern among others. Therefore, risk evaluation is used to gauge the significance of the risk to the business and whether action should be taken or not. Most organizations normally give more attention to high and medium risks and ignore low risks (Chapman & Ward, 2002, p. 5).
Risk evaluation assists the organization to operate effectively through identification of priority incidences. Identification of priority risks helps in coming up with control actions that would benefit the organization (Chapman & Ward, 2002, p. 6). According to The Institute of Risk Management (2002, p. 13), an effective risk control action must ensure that risk is either eliminated or reduced to a considerable level. On the other hand, cost effective control measures focus on the cost related to the implementation of risk management rather than the benefits. Therefore, the most effective control measure must take into consideration the cost involved and the expected benefits (The Institute of Risk Management, 2002, p. 14).
Risk evaluation is a very complex terminology. Many literatures describe risk evaluation as a process of assessing risk in the whole organization. However, a number of authors use risk evaluation as a general term for risk response. For instance, Chen, Doerpinghaus and Lin (2008, p. 40) posit that risk evaluation should focus on the whole risk factors. Beasley, Clune and Hermanson (2005, p. 524) emphasizes that risk evaluation is the last stages of risk appraisal where risk response are predicted. They add that risk evaluation entail risk prevention measures which can either be risk minimization or approval. Risk prevention measures basically involve all the activities that are undertaken to manage risks.
At a glimpse, one would think that risk evaluation is aimed at merging the results of the previous stages and decide on the best possible actions. For this reason, risk evaluation requires contribution from different stakeholders in the company including the top hierarchy in responding to risky incidences. This signifies the significance of risk reduction measures before and after commencement of a project (Kunreuther, 2002, p. 658).
According to Nacco and Stulz (2006, p. 10), risk evaluation entails three steps. The fist step is to establish a tolerable level of risk in the company. The second step is to understand the relationship between different classes of risks. The third step is to determine the action required in order to avert the identified risks. The tolerable level of risks depends on the inclination of individuals to take risks. In other words, the propensity to take risks lies in the hands of top management or those in charge of the project and therefore hard to specify.
Risk evaluation eliminates upbeat risk management. This means that reactive approaches are applied in case of risk incidences, for instance, emergency plan (Klinke & Renn, 2002, p. 1072). Understanding the relationship between various risk factors is very important in determining a single referral point for these risks. Most risks tend to be related and there are many overlaps between different classes of risks. This relationship makes the risk evaluation process very easier since the risks can be categorized according to their impact on the company (Klinke & Renn, 2002, p. 1073).
Risk Reporting
Risk reporting can be categorized into two: internal reporting and external reporting. Internal reporting is the process of communicating information obtained from risk management process to different units within the organization. Internal reporting involves the conveyance of risk management information to the board of directors, individual employees and all other departments within the organization. On the other hand, external reporting involves communicating similar information to the stakeholders (outsiders) on a regular basis (The Institute of Risk Management, 2002, p. 16).
Risk reporting in general helps the company and the stakeholders to understand the significance of the risk facing the organization and to come up with necessary policies to mitigate the impact of such risks. Risk reporting also enhances the level of awareness within and without the organization. For individual employees, risk reporting helps them to understand their accountability in the risk management process (The Institute of Risk Management, 2002, p. 17).
Risk Treatment
Risk treatment is the process of choosing and executing measures that are aimed at modifying the risk. Risk treatment basically entails risk mitigation, risk avoidance, risk transfer, risk transfer, risk diminution, risk preservation among others (Boehm, 1991, p. 32). Risk treatment is also known as risk management strategies in some literatures. All the risk management strategies (risk treatment systems) should meet certain minimum requirements. They must comply with the law and regulations of the state and the company. They must also ensure effective and efficient operations and internal controls within the organization (Beasley, Clune & Hermanson, 2005, p. 559).
Reevaluation and Monitoring
Effective risk management must have documentation and re-evaluation structure to make sure that risks are completely uncovered and evaluated and that suitable control and response measures are put in place. Therefore, re-evaluation and monitoring process entail periodic auditing of the policies and standards and review of their performance to identify opportunities and threats (The Institute of Risk Management, 2002, p. 18). Evaluation and monitoring process take into account the fact that organizations and their environment are always dynamic in nature. For this reason, the systems are normally adjusted to fit the changes in the organization and the environment in which the organization operates (The Institute of Risk Management, 2002, p. 19).
The monitoring process makes sure that suitable control measures are in place and that the risk management process is well understood and adhered to. In addition, re-evaluation and monitoring process provides assurance that the procedure and the information used are appropriate. They also ensure that the adopted measures are the one that were originally intended. Lastly, they help to reach better decisions and to acquire new knowledge that could be useful in future management of risks (Kunreuther, 2002, p. 660).

The value tree model in figure 3 shows the types of risk management techniques that are generally applied by various organizations.
Information Systems for Risk Management
One of the principle factors to successful risk management is the idea of risk management based on information systems that utilizes information flow (Holt 2006). Companies that lack efficient and effective risk management information systems have found it very difficult to identify, assess and control risks. This is even worse among the multinational corporations in which risk management is linked to investment projects spread across the globe. Therefore, an efficient and effective risk management information system is the one that matches the business model (Stapleton, 1997, p. 5).
According to Maurer (2008, p. 28), an effective and efficient information system must take the following factors into consideration: information request, sources of information, and significant processing steps of acquiring output from the input. Information request corresponds to the intended output from a system. This is the stage of any information system where the specifications of the vital reports are made. The specifications include certain aspects of the information content, forms of output and blueprint, time limit, and the targeted individuals (Maurer, 2008, p. 29).
Information source encompasses all the sources of information used to sate information request. In addition, Information sources represent internal and external sources of information for any business entity (The Institute of Risk Management, 2002, p. 20). Lastly, the vital steps of acquiring output from input entail algorithms as well as the entire equipments and resources used within a given setup. It also includes system applications and modules (The Institute of Risk Management, 2002, p. 22).
Objective and Requirements of Risk Management Information System
Even though different companies have different views and standards regarding risk management information systems, there are certain requirements that apply to all businesses (Beynon-Davies & Williams 2003, p. 37). Effective risk management information systems entail more than just the storage of chronological and accurate data regarding business losses. It involves the provision of necessary assistance in the whole process of risk management starting from risks analysis and aggregation although risk reporting, risk treatment to re-evaluation and monitoring. It also entails the processing of economic data of the organization that are unrelated to the risk itself, for instance, investment portfolios that are aimed at mitigating risks. For these reasons, risk management information systems are highly integrated and is capable of accessing other components of the overall information system, for instance, accounting information (The Institute of Risk Management, 2002, p. 24).
The information systems must have a communication interface to make sure that there is a smooth and efficient communication and information flow among various stakeholders in the company, especially those involved in the risk management process. One of the techniques used to achieve this is the establishment of data reports at different points at different fronts depending on the profession and experience of the targeted individuals (The Institute of Risk Management, 2002, p. 25). Many literatures differentiate the requirements of risk management information system in the following categories: economic and procedural requirements, technical requirements, and requirements on investment safety in the software packages and associated costs.
Economic and Procedural Requirements
The most important economic and procedural requirement is the description and ease of access to checklist to identify the key risk factors. Risk inventory enables the company staff and other stakeholders to have a general view of the risks at any time (Chapman & Ward, 1997, p. 14). The risk inventory also provides a specification of preferences for various risks, for instance, it defines and assigns different classes of risks that are relevant to the business. The different classes of risks are normally assigned to an individual ‘risk owner’ who is responsible for them. Economic and procedural requirement necessitate definition and assignment of parameters for each form of risk (Chapman & Ward, 2002, p. 65). Another economic and procedural requirement is the structured overview of the remedies of the key risk factors, for instance, the company’s established insurance covers (Chapman & Ward, 1997, p. 16).
The risk management information system should also incorporate a framework for controlling, reducing or transferring risks (Chapman, 1998, 342). These measures should be harmonized with other strategic planning system in the organization. The system used has to be flexible in the quantitative definition of risks, for example, it should highlight other alternatives available for quantitative descriptions. The system should identify the relationship between various types of risks for simulation purpose (Chapman, 1998, 343).
An effective risk management information system also requires well defined statistical methods to compute the overall risk position of the company, for instance, Monte-Carlo simulation method. The system used must provide alert indicator to warn in case of important developments of risk factors. Last but not least, the system must have the capacity to expand the risk register that covers all the departments within the organization, for instance, finance, human resource, stores among others (The Institute of Risk Management, 2002, p. 26).
Technological Requirements
First, the risk management information system used must have the capacity to reflect diverse structures within the organization and integrate the workflow. The actual data should always be available and accessible in the system at all the time. The accessibility can be facilitated through import/export data interface. The system must have reporting mechanism for all types and classes of risks and the mechanism should be tailored for the intended target or user, for example, e-mail alerts. The risk reports have to be transparent and should be available and accessible to outsiders who have an interest in the company (stakeholders). Lastly, the system must incorporate authorization and data security concepts (The Institute of Risk Management, 2002, p. 25; Beasley, Clune & Hermanson, 2005, p. 566)
Software Safety and Associated Cost Requirements
Before acquiring and installing any risk management information system companies must take into consideration the size of the software company and its future strategies. The experience and technical know-how of the software manufacturer is also very important. Other important factors to be considered are the clients and references of the software company. This will help to assess the credibility and experience of the software company (The Institute of Risk Management, 2002, p. 26). The software company must also be willing and ready to provide support service and installation of the software packages. Other additional factors include licensing costs, cost of personalizing the software, cost of maintenance and installation, cost of training the staff who will be using the software among others. After evaluating and reviewing all these factors, a company can enter into a long-term mutual relationship and an agreement with the software company (Beasley, Clune & Hermanson, 2005, p. 566).
Conventional Layout for Risk Management Information System (RMIS)
The principle concern for risk management is the management of information. In most cases the information is very much available in the company’s database or in different departments within the organization. Therefore, risk management information system mainly entails generation and maintenance of the information flow and communication between different units of the company and among the stakeholders. In addition, it also involves a unified processing of information in accordance with the conventional risk management standard (The Institute of Risk Management, 2002, p. 27). Figure 5 below show a layout of information systems for the investment risk management. The figure shows how data is transformed into vital information during various stages of decision-making.
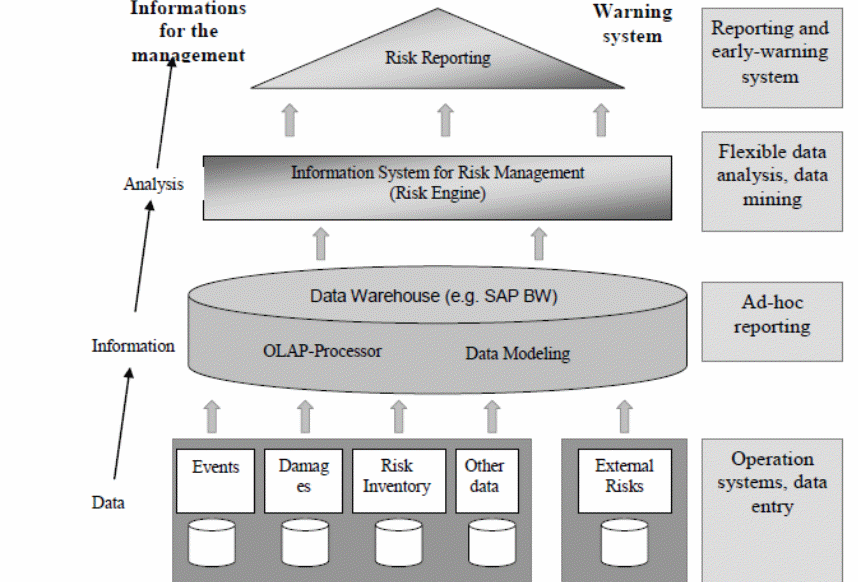
The figure highlights the most significant constituents of information request and information basis. In addition, it shows the main tools and technologies that support the transformation of inputs into output (risk reports). The output or risk reports represent the initial warning and should be backed by additional information to support the decision-making process (The Institute of Risk Management, 2002, p. 28). Figure 6 represents informatics solutions for investment risks. The conventional risk management information systems can identify dat6a sources and provide accurate results/ comprehensive report using the available data. These systems are divided into the following components/module: access to data source systems module, risk identification and system module, risk aggregation and consolidation module among others (Maurer, 2008, p. 30).
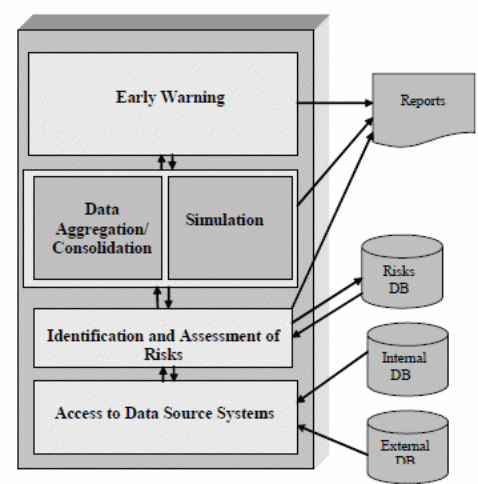
The access to the data source module is the link between the internal and external databases. This module is prominent in risk management information systems using relational databases. The component is responsible for the transfer of raw data that is vital in the initial stages of the risk management process (risk assessment and analysis). In the case of investment risk management, the module plays a major role in market analysis studies, and acquisition and accumulation of macroeconomic data and external reports among others. Generally, the module also plays a role in the identification and assessment of the companies’ historical data (Maurer, 2008, p. 32).
Risk identification and assessment module organize the risk databases from the previous module to develop a risk inventory that would make it easier to describe and assess risks (Maurer, 2008, p. 32). On the other hand, risk aggregation and consolidation module entail all the modus operandi which merges the primary data through consolidation or aggregation, hinging on certain requirements for the classification of various types of risks. Simulation models are specifically designed for specific functions or models, for instance, the Monte-Carlo simulation. Simulation module helps to determine the overall risk position of the companies and attributes of these risks. This module generally achieves this through statistical indicators and pictorials/ visualization tools (The Institute of Risk Management, 2002, p. 29).
The early warning component is responsible for keeping an eye on the development of risk elements and warning those responsible in time regarding the development of the risk factors using statistical indicators availed in the form of reports. The module should be backed up with the right data management solution, for instance, administration system (Maurer, 2008, p. 33).
Different Categories of Data in RMIS
Generally, risk management information systems have three categories of data and these are internal data, external data, and risk specification data (Smith & Merritt, 2002, p. 20). Internal data are widely known as “internal DB” which means internal data base. Internal data include the actual and historical data stored within the company databases. These data can be classified into different classes or integrated in data storage. On the other hand, external data widely known as “external DB” meaning external database represents all the data that are accessible and available to stakeholders or business partners. They also represent data that are shared among organizations or public databases. They also include data that can be accessed through subscription (Smith & Merritt, 2002, p. 23).
Risk access data are generally known as “Risk DB” which means database for various risks existing in the company (Smith & Merritt, 2002, p. 23). There are diverse methods of accessing risk data that exist in the company and this depends on the database management system used to create and preserve data repository. As already mentioned above, most of the risk management information system use relational database system. As a result of this, most developers have access to various types of relational data source linkage technologies, for instance Open Database Connectivity for Microsoft systems and Java Database Connectivity for Sun systems. All of these systems depend on the type of software used (Smith & Merritt, 2002, p. 24).
For data repository that are organized in non relational database systems or inherited systems existing in the company, access can be designed in an Extended Mark-up Language (XML). XML is widely accepted among global enterprises for integrating data. Data Extended Mark-up Language can also be organized in accordance to the relational data model. In this case, the company is at discretion to choose the best relational database system it prefers. There are two common databases: desktop and server databases (Maurer, 2008, p. 34).
Desktop databases are used essentially on local networks, for instance, Microsoft access or individual workstations. On the other hand, server databases are used on the wide area networks or integrated workstations. Nevertheless, before a company makes any decision regarding the system design to adopt it has to consider the fundamental risk management information system requirements mentioned above. However, the significance of each system varies from one company to another (Maurer, 2008, p. 36).
Implications of Risk Management Information System (RMIS)
Over the recent past many companies have invested a lot of money to develop risk management information system. These systems gather all-round data on the company’s position in terms of risks and work out mathematical measurements, for instance, Value at Risk, to determine the level of risks faced by the company. However, the use of risk management information system goes beyond statistical measurements. Risk management information systems are now being used in capital allotment and incentive reimbursement (Williams & Cockburn, 2003, p. 43).
Many authors in the past have explored how information systems for risk management have improved risk management for investment/financial companies through the adoption of latest measurement techniques. These authors also explored the trade-offs between latest risk measurement techniques and how they are the trade-offs depend on information system design (Cockburn, 2001, p. 31). However, some experts argue that information communication technologies alone cannot solve all the risk problems (Porthin, 2004, p. 45).
Risk management information systems improve accountability and information flow within the organization. Accountability is a fundamental management tool that is used to prevent and patch up problems in the organization. The risk management information system improves accountability and information flow through wider dispersions, interfaces, distant effects and controlled events (Williams & Cockburn, 2003, p. 44). Risk management information systems ensure that information is widely spread and accessible to all the stakeholders especially in a networked system. This is very crucial among multinational corporations with branches spread across the globe (Cockburn, 2001, p. 31).
Interfaces are the core of all the information communication technologies, particularly networked systems. Given the complexity and diversity of interfaces within a networked system it is very difficult to identify the source of a problem or who is responsible for particular risks. However, with the advent of object-oriented software in risk management information systems the problem of system interfaces have been minimised. For this reason, it is currently possible to establish the source of risks in an organization with numerous and diverse networked systems (Maurer, 2008, p. 37). Distant effect is also characteristic of networked systems. The breaches of these systems have serious repercussions for the company. All of these have been improved by the current risk management information system software. Therefore, it is not easy to steal information under the current technologies without a trace (Maurer, 2008, p. 39).
Rare events are very difficult to control. This is particularly true for companies operating in a hostile and competitive environment. Risk management information systems are designed to warn individuals on a day-to-day basis and therefore take care of unexpected scenarios or events (Cockburn, 2001, p. 31). Networked risk management information systems are well adapted to alleviate risks through accountability. Accountability is enhanced through routine auditing, hierarchical control, legal liability, and insurance (Chorafas, 2008, p. 23). Risk management information systems are designed in a way that auditing can easily be carried out to supplement hierarchical control. Legal liabilities hold software developers accountable for any security vulnerabilities. For this reason, risk management information systems like other systems enhance information security within an organization (Maurer, 2008, p. 39).
According to Chorafas (2008, p. 25), risk management in information systems encourages reporting of risk incidents. Incidents in this case not only encompass errors and oversights, but also include “near misses”. Therefore, risk management information systems help to detect events that are very difficult to notice and can cause massive damage to the company. At times incidents are unreported even when they are noticed and these are attributed to a number of reasons. For instance, most employees fail to report these incidents for fear of victimization. Failure to report these incidents is bound to cause more damage especially in large organizations. Risk management information systems encourage risk reporting through risk alerts and routine reports (Chorafas, 2008, p. 26).
The new risk management information systems have made it easier to generate data and maintain information flow among different units of the company. The systems are able to gather and accumulate data both internally and externally within a short period of time (Cockburn, 2001, p. 32; Wiegers, 1998, p. 40). The external and internal data are linked together using access to the data source module. Access to data source module has made it easy to identify and assess historical data. The current information systems have a huge capacity and are able to store large quantities of risk data. The data stored in the database are easily retrievable and are secured (Wiegers, 1998, p. 41).
The risk classification and appraisal module not only help to develop a risk inventory but also to describe and assess risks. The system is able to consolidate and aggregate risk data in accordance with the conventional requirements (Williams & Cockburn, 2003, p. 39). Risk management information systems have made it very easy to detect risks at very early stages. The early warning module has been used to keep an eye on the development of risk elements and warning those responsible in time regarding the development of the risk factors using statistical indicators available in the form of reports. Risk management information systems therefore have considerably reduced the cost of auditing in most companies (Maurer, 2008, p. 33).
Risk Management Information System Obstacles
The principle reason why many companies have not embraced risk management information system is the significant cost involved in acquiring, installing and maintaining these systems (Porthin, 2004, p. 45). The cost of the state of the art information communication technologies is relatively high and therefore most companies have resorted to traditional ways of managing risks. In other words, many of these companies rely on qualitative approaches rather than quantitative approaches. Qualitative approaches are subjective in nature and are based on individual experience and perception. On the other hand, quantitative approaches are objective in nature and based on mathematical and statistical assessment (Schwalbe, 2000, p. 6).
Another obstacle is the cost of consolidating and evaluating information from different units within the company. Information cost encompasses the cost of transmission, recording and processing data as well as the cost of time lag caused by delays in assembling and verifying data (Porthin, 2004, p. 48). Even though these costs are minimal in highly automated systems, the efficiency rate of these technologies depends on their specifications and the software developer. The cost of information mainly affects consolidated systems. For instance, some companies may be forced to manage different units or branches separately if the cost of information in an integrated system is high (Cockburn, 2001, p. 32).
Another obstacle to risk management information system is regulatory costs. Regulatory cost encompasses software license (limits use of certain software), financial regulations that discourages massive spending on a single project, financial conditions of the company among others (Williams & Cockburn, 2003, p. 42). In addition, some companies normally experience a problem of quantifying data. This always arises due to lack of consensus among the team members on the best approach to use. Some may prefer to use probability-weighted approach while others may prefer to use scenario analysis approach (Schwalbe, 2000, p. 10).
Methodology
Population and Respondents
This research employed a structured survey to collect data from participants. The data were collected through the use of structured questionnaires. The participants were selected from the organisation using random sampling method. The entire company was too large to undertake a research of this nature. Consequently, the researcher used a random sampling method to select three key employees from the IT department, human resource department, administration department and accounts department. Thus, a total of 12 respondents were selected. What is more, these departments were selected intentionally since they are thought to be more conversant with the topic under investigation. The case study approach was used in this study in order to gain deep knowledge regarding the role of information system (ERP) in mitigating risks facing the selected organization. According to Eisner (2001), the case study approach is suitable for an explorative study since it allows the research to compare empirical observations with relevant theories. The relevance of this approach has also been acknowledged in various studies focusing in other social sciences (Scapens 1990; Eisner 2001).
Data Collection
The current research used both primary and secondary data for the relevant information. Primary data refer to the raw information collected by the researcher whereas secondary data refers to the materials already collected by other researchers (Bryman & Bell 2007). The questionnaire is the basic instrument that researchers use to collect primary data. Secondary data was collected from diverse sources including books, journals and articles. The researcher also used relevant materials from the internet. In addition, both the quantitative and qualitative approaches were employed in the current research. The qualitative approach enables a researcher to gain insight regarding the issue under investigation (Chapman & Ward 2002). The quantitative approach can also be used to analyse the impact of information systems on the risk management processes of a firm. Consequently, the current research is both descriptive and explorative in nature since the researcher will investigate, describe and explain how information systems can be used to mitigate risks facing the Rolls-Royce Company.
Primary Data
The current study employed primary data in order to gain insight regarding the topic at hand. In order to collect primary data, questionnaires were sent to a number of people working at the company. The researcher selected people who were in a position to provide relevant information to the study. The questionnaires were sent to personnel working in the human resource department, administration department, accounts/finance department and IT department. The researcher opted to use primary data since it provides first-hand information regarding the topic being investigated. Primary data are collected for a specific reason and used to resolve a specific problem. Bryman and Bell (2007) state that the primary data allows the researcher to not only focus on a specific issue but it also grants him/her autonomous control regarding the manner in which such data is collected.
The researcher prepared a semi structured questionnaires which contained both open-ended and close-ended questions. Semi-structured questions were used because the researcher did not adhere to any particular order. In addition, the semi structured questionnaire consists of formal questions framed and customized to suit the research objectives. The researcher sent the questionnaires to the selected participants via the e-mail. According to the researcher, the early distribution of questionnaires would give the respondents sufficient time to meditate thoroughly prior to responding to these questions.
Secondary Data
Secondary data was collected via meticulous and extensive internet search for information pertaining to the subject at hand. The researcher employed various navigators such as www.googlescholar.com, www.google.com, and bibsys to search for information on key words such as information systems, risk management and names of prominent professors and scholars related to the concept. The internet search led to different articles, books, journals and other publications. Nonetheless, it was difficult to find a book that specifically addresses the topic. It is against this backdrop that the researcher opted to interview experts in this area in order to acquire all the materials required for this dissertation.
The researcher opted to integrate secondary data in the current study for a number of reasons. First, secondary data saves time and cost. The researcher merely uses information collected by others in his/her study. Second, secondary data is of superior quality. Consequently, the researcher can analyze and reanalyze the data to generate new ideas. Nonetheless, secondary data have some disadvantages. According to Bryman and Bell (2007), secondary data are complex and outdated. What is more, the researcher does not have control over their quality.
Method of Data Analysis
This section focuses on the concrete analysis and discussion of the data collected. The researcher carried out a literature review and data analysis in order to get better results. According to Andersen (1998), a comprehensive and logical data analysis must be performed in order to realize a good result. The researcher analysed data using both the quantitative and the qualitative methods.
Reliability
The reliability of data is subject to the nature of the measures adopted. Thus, it is crucial for the researcher to be accurate to get reliable data. In addition, the researcher must provide a detailed account regarding the manner in which the measures were carried out in order to augment the reliability of the data. This is an important aspect given that other researchers will eventually use the same data for analysis purposes. According to Cook and Campbell (1979), reliability refers to the constituency in the measurements adopted by the researcher.
Validity
Cook and Campbell (1979) suggest that the validity of data depends on the potency of propositions, inferences and conclusions. Data is assessed in order to establish the validity and significance of the topic under investigation. Validity is concerned with establishing whether the data collected is applicable to the topic being examined and whether the interview performed provided answers to the problem. In this study, the researcher will postulate that the theoretical understanding of information systems and risk management is the same as in the operational sense. To that extent, there is a constituency between the two variables. The researcher perceives a clear relationship between the practical and theoretical notions of information systems and risk management and for that reason; we can say that the data is valid.
Case Study: Implementation of Erp at Rolls-Royce
This section discusses the implementation of ERP/SAP at Rolls-Royce Company. This section starts by presenting the background information of the company. This will be followed by a discussion on the Company’s IT status prior to the implementation of system applications and products (SAP). Finally, this section will discuss the current situation after the implementation of SAP.
Company Background
Rolls-Royce is a leading manufacturer of aircraft engines. The Company was readmitted to the private sector in 1987 and purchased Northern Engineering Industries two years later. Rolls-Royce was able to use the newly acquired asset to strengthen its capabilities in the field of industrial power. In 1995, the Company consolidated its presence in aero propulsion and industrial gas turbines after acquiring the US-based Allison Engine Company. Rolls-Royce was able to use this asset to augment its presence in the United States market. The Trend series is currently the state-of-the-art and most powerful family of engines manufactured by Rolls-Royce. The Trend series are mainly used to propel the Airbus A340-350. These engines are not only powerful but also require minimal maintenance and operating outlays. The Power Generation Market of the Firm consists of both nuclear and electric power. The firm has also made substantial investments in marine applications (i.e. Creating power plants for naval and nuclear vessels). It is widely acknowledged that Rolls-Royce is an International Company that produces a wide array of first-rate products. The firm owns manufacturing and assembling plants in more than 12 countries. In addition, it offers first-class (after-sale) services which include mechanical repair and distribution of spare parts (Yusuf, Gunasekaran & Abthorpe 2004, 255).
The Situation prior to ERP/SAP
The Company employed over 1400 systems prior to the adoption of the ERP/SAP system. These systems were not only costly to manage but also difficult to develop and maintain. In many cases, these systems failed to produce precise and reliable information needed for making accurate and timely performance evaluation such as quality metrics. Most of these systems were moribund and therefore could not adapt well to the contemporary manufacturing setting. For example, Yusuf, Gunasekaran and Abthorpe (2004) reported that “some of the legacy systems were so old that they had year 2000 compliance problems… Work within Rolls-Royce was functionally oriented and various departments worked in isolation” (p. 255).
MERLIN (mechanized evaluation of resources, logistics and inventories) was the last major system that the Company developed in 1980s to handle manufacturing processes. The manufacturing system was essentially a scheduling system that subscribed to the manufacturing resource planning (MRPII) standards. Although the system was somewhat productive, it was susceptible to physical manipulation. In addition, the system did not facilitate efficient communication between different plants. For example, there were communication mishaps between MERLIN and IBIS (inventory based instructing system) systems on a regular basis. For example, the Ansty and Bristol facilities employed the moribund IBIS system in their respective manufacturing process. What is more, the dilapidated manufacturing system (IBIS) exhibited inefficiencies in tracking the WIP (work in progress) between different facilities leading to stock-taking problems (Yusuf, Gunasekaran & Abthorpe 2004, p. 256).
The corporate cost accounting (CCA) was another information system that the Company employed to monitor financial transactions. What is more, the Company had several information systems for examining and managing procurement, financial and commercial systems. Nonetheless, these systems could not be synchronized because they had different file formats and databases. Thus, Rolls-Royce was not able to use MERLIN to launch direct communication with suppliers, partners and clients. To be precise, these information systems did not sustain substantial business growth since they were not able to adapt to the changes in the business environment (Yusuf, Gunasekaran & Abthorpe 2004, p. 256).
Information System at Rolls-Royce
Rolls-Royce and Electronic Data Services (EDS) entered into a partnership in 1996 whereby the former subcontracted its IT department to the latter. Under the partnership agreement, the IT firm (EDS) was expected to design and maintain the IT systems of Rolls-Royce. In 1998, the IT firm redesigned the structural hierarchy of the Company. For example, the CFBU (consumer focused business units) was assigned the role of managing sales transactions in different segments of the market. Similarly, the OBU (operational business units) provided the logistic support for manufacturing products. Finally, the Executive Group was responsible for the overall management of the entire business at the Company (Yusuf, Gunasekaran & Abthorpe 2004, p. 256).
The EPR/SAP Project Implementation
The enterprise resource planning project comprises of a management team and SAP experts from the EDS Company. The ERP/SAP project also consists of expert staff and internal supervisors with critical knowledge and experience relating to the old internal systems and cross-functional business units. What is more, there is an ERP/SAP planning team for each OBU which ensures that the training and working adjustments are implemented properly. The ERP/SAP project was expected to address three key risks facing the Company (Yusuf, Gunasekaran & Abthorpe 2004, p. 257).
Cultural Risks
The new ERP/SAP system was expected to receive wide acceptance since it offered Rolls-Royce superior functionality compared to the legacy system. Nonetheless, some processes and functions of the ERP/SAP system did not gain full acceptance the MERLIN system previously had. The project team resolved this problem by demonstrating the benefits of the ERP/SAP system to the firm such as alleviating the conventional segregation between the OBU and business departments. The ERP/SAP implementation plan was upgraded in order to deal with the cultural changes. The training program was conducted in two phases. The first phase entailed technical training performed by the SAP experts. During the second phase, the EDS experts collaborated with the SAP consultant to train Rolls-Royce employees on how to use the new system. The training program was integrated with workplace presentations and demonstrations to convey information to all Rolls-Royce staff about the benefits of the ERP/SAP system (Yusuf, Gunasekaran & Abthorpe 2004, p. 257).
Technical Risks
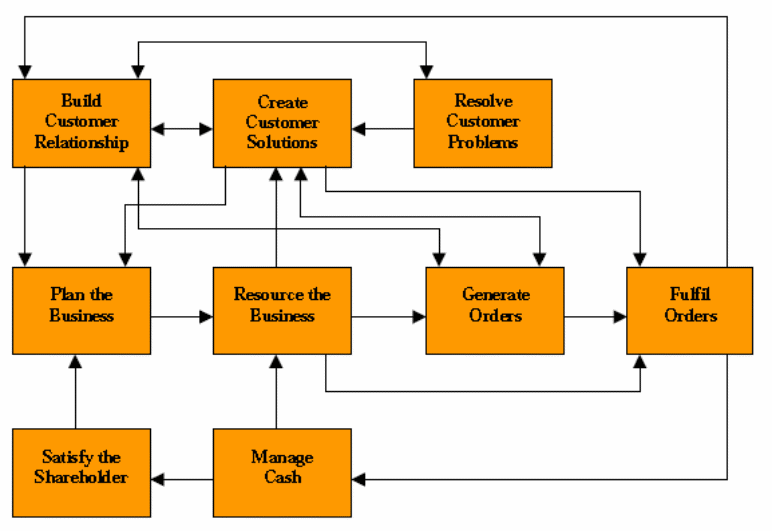
Data accuracy is a major technical risk facing Rolls-Royce Company. The new ERP system entails the reclamation of old data from the old systems. This data must be standardized, screened and stored in a prudent format within the new ERP/SAP data repository. In addition, Rolls-Royce faced risks associated with data duplication. Consequently, the IT firm (ECD) developed interfaces between the ERP/SAP system and the old system to facilitate efficient data transfer. There are nine core business processes that take place at Rolls-Royce. Figure 1 depicts the business interfaces and processes at the Company. The new ERP/SAP system was implemented for a number of reasons. These include resolving customer problems, building customer relationships, fulfilling customer orders, and managing cash flows.
Results and Discussion
Results
The researcher selected 12 people from Rolls-Royce Company to take part in the study. The participants were asked questions relating to their previous knowledge and experiences about information system projects. Their responses are summarized here and the conclusions derived from the interview findings are presented in chapter six.
Project Launch, Planning and Progress
Four interviewees noted that the launch of the ERP/SAP project was quite successful. However, one participant mentioned that the objectives of the ERP/SAP project were not concrete during the project launch. It was noted that the planning phase of the project focused more on technical issues at the expense of other salient aspects. The implementation team simply wanted to replace the legacy system with the new ERP/SAP system. The team ignored the fact that the new (ERP/SAP) system would result in substantial adjustments in a number of business processes. Seven interviewees mentioned the planning and scheduling phases presented the major setback in achieving a robust ERP/SAP system capabilities to alleviate risks facing the Company. For instance the duration of the initial planning phase was 10 months. However, the duration of the planning phase was extended by two years. The respondents from the HR department noted that the initial timetable was impractical since they had prior experience of the business processes at the Company. Nonetheless, one of the respondents asserted that he would rather wait for a longer time in order to acquire a fully-functioning system as opposed to using a system that was hastily developed. The respondents stated that they needed an efficient system that could guarantee data protection, efficient supply chain system and customer satisfaction.
All interviewees concurred that the continuous alteration in the project schedule compromised the reputation of the ERP system. For example, four interviewees noted that the constant delays had a negative impact on the end-user training program. The interviewees also noted that the constant delays affected the morale of some employees towards the new system as well as its applicability in mitigating business, technical and operational risks.
The ERP/SAP Project and Business Departments
All interviewees stated that the ERP system was important in the entire business departments of the Company. It was observed that the legacy systems (MERLIN) deserved to be replaced by the ERP/SAP system. One of the interviewees noted that “the new system is a critical step that will transform Rolls-Royce into a global organization since it will provide a uniform platform of conducting business”. Another respondent mentioned that “the ERP/SAP system will promote the internal communication thus enabling Rolls-Royce to manufacture a wide range of products at different locations”. However, one participant mentioned that the link between the practical and the theoretical aspect of the ERP/SAP system was somewhat fragile because of the minimal participation of both the managers and end-users from various business departments. For example, one interviewee from the HR department stated that both managers and end-users from different business sectors should have been assigned greater roles such as developing specifications of the ERP/SAP system.
Nine out of the 12 respondents agreed that the new system would mitigate risks apparent in the business departments. The interviewees from the administration department and IT department mentioned that the new system will be a strategic instrument in mitigating risks facing the Rolls-Royce. It was also mentioned that the major advantage of the ERP system will be in enhancing in the quality of information. For example, one interviewee from the IT department had this to say, “the ERP/SAP system has a warehouse with a reasonable user-friendly interface that permit end-users to retrieve data required to make sound managerial and business decisions”. However, another interviewee from the accounts department mentioned that the confidence and expectations in the new system would be lower due to the project holdups as well as the presence of bugs in the system. Another interviewee observed that given that the major users (IT department) were reluctant to attend training is sufficient proof that no one desires to be associated with the new ERP/SAP system. Nevertheless, the majority of the interviewees agreed that the ERP/SAP system would play an important role in alleviating risks facing the Company.
Opinions on Communication and Training
The majority of the interviewees mentioned that the new system would be successful in risk management if information pertaining to the new system was communicated appropriately to the relevant stakeholders. One interviewee mentioned that the new systems had an efficient communication system that would allow all business departments to detect and alleviate potential risks. Another respondent noted that, “the ERP/SAP system will facilitate efficient management of inventory levels, supply chain systems and fulfilment of customer orders”. The interviewees generally agreed that the new system would diminish interruptions to the flow of communication and information, reduce overhead costs and enhance data security within the firm. One interviewee from the IT department stated that “the ERP/SAP system will reduce risks emanating from abuse, waste, fraud and mismanagement thereby facilitating the smooth management of the firm in realizing its strategic goals”.
All the participants agreed that the training program was important because it would help end-users employ the new system effectively in risk management. Eight interviewees asserted that the training program for the end-users was effective in explaining the benefits of the new system in risk management. On the contrary, one respondent felt that the training program for the new ERP/SAP system was not comprehensive because the trainers provided insufficient materials relating to the whole solutions provided by the system. What is more, all the respondents stated that the training period (two days) was not sufficient to allow the end users gain adequate training on the new system. Nonetheless, the majority of the respondents agreed that if the training period was extended and the benefits of the ERP system clearly communicated to the end users, it would be readily accepted.
Discussion
The main theme of this dissertation was to investigate how information systems benefit the process of risk management. The literature review section has shown that the human factor (i.e. Employees) is an integral part of information systems in handling risk management. This research used Rolls-Royce as a case study to demonstrate the role of information systems (ERP/SAP) in the process of risk management. A majority of the interviewees agreed that the new information system (ERP/SAP) will be instrumental in mitigating risks facing Rolls-Royce.
Rolls-Royce is a multinational company with a huge composite business process. Nevertheless, the size of the company has brought about administrative complexities relating to the management of the Company’s global business operations. It is against this backdrop that the Company decided to replace the old MERLIN system with the new ERP/SAP system in order to mitigate the strategic and business risks effectively. The ERP/SAP system was also expected to mitigate business risks associated with the rising number of customer orders. Rolls-Royce manufactures a variety of first-rate turbine engines. Consequently, the Company’s management team has acknowledged the need to adjust business processes in order to maintain its position as the major player in the defence and aerospace industry. Thus, the company realized the need to adopt an efficient information system (ERP) in order to improve communication with suppliers as well as fulfil customer orders (Yusuf, Gunasekaran & Abthorpe 2004, p. 265).
The new system has necessitated the development of a Data Warehouse-an assimilated data that is stored in a single location and is mined from external, historical and operational databases. The data is usually monitored, amended and normalized for future retrieval. The data warehouse has a reasonable user-friendly interface that permits managers and employees to generate database queries. For example, senior managers can use these queries to retrieve management data required to make sound managerial and business intelligence decisions. Thus, the ERP/SAP system can mitigate risks associated with supply chain process and unfulfilled order requests. Yusuf, Gunasekaran and Abthorpe (2004) mention some of the benefits associated with the ERP/Sap system. For instance, the researchers state that the new (ERP/SAP) system can reduce costs incurred by the IT department.
It can also augment the ability of the firm to promise and fulfil customer orders on time. It is worth mentioning that the old system could not guarantee the delivery of customer orders on time because it had several technical problems. On the contrary, the new system can augment the confidence and satisfaction levels of customers since it ensures that orders are processed and delivered on time. What is more, the relationship within the Company’s global supply chain will improve since the new information system has an electronic platform to carry out business transactions. Thus, Rolls-Royce expects the new information system to improve the Company’s sales revenues in the near future (Yusuf, Gunasekaran & Abthorpe 2004, p. 265). This means that the implementation of the ERP/SAP will ensure that risks associated with unfulfilled customer orders and supply chain system will be mitigated.
The current research has also demonstrated the importance of upgrading information systems on a regular basis in order to handle emerging business risks successfully. The situation at Rolls-Royce demonstrates the relevance of this statement. Initially, Rolls-Royces used the MERLIN system to manage its manufacturing processes as well as coordinate other business process. However, the system was not able to mitigate a number of operational risks facing the company. For example, the MERLIN system did not facilitate efficient communication between different sites. There were communication mishaps between MERLIN and IBIS (inventory based instructing system) systems on a regular basis. What is more, the Ansty and Bristol facilities employed the moribund IBIS system in their respective manufacturing processes. The IBIS system also could not track the WIP (work in progress) between different facilities leading to sock-taking problems (Yusuf, Gunasekaran & Abthorpe 2004, p. 256).
In a nutshell, the MERLIN system was too old to cope with emerging business challenges/risks. The adoption of the ERP/SAP system facilitated an efficient process of risk management within the Company. As mentioned by several interviewees, the new system can synchronize the Company’s global supply chain system as well as different manufacturing facilities thus ensuring that customer orders are processed and delivered on time. In essence, the new system has mitigated operational risks that were apparent in the old (MERLIN) system. The ERP/SAP system ensures that different manufacturing facilities and the supply chain system are well coordinated and executed.
Some respondents mentioned that the new system would curb the risk of unauthorized access to the confidential information of the Company. According to previous studies, many business organizations have reported incidences of unauthorized access to their databases (Schneier 2000; Berkowitz 2003). The previous information system (MERLIN) was susceptible to physical manipulation which meant that rival firms could easily access confidential data of Rolls-Royce. What is more, poor supervision of the entire system can result in unauthorized access to confidential data (Axelrod 2003, p. 10). The new ERP/SAP system consists of a Data Warehouse-an assimilated data that is stored in a single location and is mined from external, historical and operational databases. The data is usually monitored, amended and normalized for future use. Thus, the new system can mitigate the risk of unauthorized access to the Company’s database since it allows end users with a unique access code to access confidential information. According to some respondents, the new system (data warehouse) has a user-friendly interface that permit end users to retrieve data required for making sound management and business intelligence decisions.
The literature review and the case study have demonstrated that information systems can only be effective in the process of risk management if they get support and commitment from the relevant stakeholders. A majority of the interviewees mentioned the need for enhancing a better understanding regarding the role of ERP/SAP in the processes of risk management. The view that individuals from different business department do not communicate well has been recognized in this study as an elementary issue that can affect the capability of the new information system in mitigating business risks facing Rolls-Royce. This finding supports the results of the study conducted by Jern (2009) regarding the significance of reciprocal communication among various business departments in ensuring that the information system facilitates the process of risk management. Previous studies have also highlighted the importance of providing all stakeholders with relevant information pertaining to the new information system to facilitate acceptance (Nah & Delgado 2006; Mandal &Gunasekaran 2003; Mabert, Soni & Venkataramanan 2003).
As mentioned in the literature review, information systems can benefit the process of risk management within a company. A majority of the interviewees also agreed with this statement. Therefore, the management must take into consideration views from all business departments before investing in information system applications. What is more, the IT departments must work together with other departments (i.e. Human resource department) prior to the implementation of an information system. Such collaborations will ensure that the information system will be accepted by all stakeholders as a key instrument in mitigating internal and external risks facing business organizations.
The literature review and the interview findings suggest that the competence of the end users is another key factor that can determine the success of an information system in mitigating business risks. Consequently, there is an urgent need to execute proper training programs as well as mechanisms of knowledge transfer to facilitate the proper functioning of the new information system. A number of interviewees mentioned that the training program was too short and did not cover all the relevant aspects pertaining to the new information system. Therefore, the current research suggests that business organizations in the manufacturing, health and energy sectors would benefit immensely by training their staff on how to use information systems in the process of risk management.
Summary, Conclusion and Recommendations
Summary
There is no doubt that risks are part and parcel of any business activities. They include strategic and operational risks, human risks and market risks. If appropriate remedial measures are not implemented, these risks (both internal and external) may result in substantial losses and render an organization ineffective. Currently, many business organizations have adopted a variety of information systems in their risk management processes. The main aim of this dissertation was to investigate the role information systems in the process of risk management. Rolls-Royce was used as a case study to explore the benefits of ERP/SAP system in the process of risk management.
The main objective of this dissertation was to determine how information systems benefit the process of risk management in a real organization (Rolls-Royce). The minor objectives covered in this study were:
- To determine how information systems boost risk assessment.
- To analyze how information systems enhance the effectiveness of risk control.
Risk is defined as “the combination of the probability of an event and its consequences” (IRM et al., 2002). According to the International Federation of Accountants, risk refers to “uncertain future events that could influence the achievement of the organization’s strategic, operational and financial objectives” (IFA 1999). The Institute of Electrical and Electronics Engineering (IEEE) defines information systems (IS) as an array of components that are arranged in a manner that augments the implementation of some functions (IEEE1990).
According to Nickerson (2000), information systems are made up of technical components (i.e. Computers), information, processes, and people. The Committee on National Security Systems (2006) defines an information system as “a set of information resources used to collect, store, and process, maintain, use, share, disseminate, dispose, display, or transmit information”. What is more, Wognum et al. (2004) assert that the purpose of the information system is to augment information requirements of firms. There are various types of information systems that business organizations use to mitigate risk. They include: Supply Chain Management (SCM) systems, Customer Relationship Management (CRM) systems, Product Data Management (PDM) systems, and Enterprise Resource Planning (ERP) systems. Risks are apparent in various organizational activities such as technology, finance and other strategic operations of a firm. To be precise, risks may result in ruthless interruption of information flow, considerable decline in financial assets and other physical adversities. What is more, mismanagement and fraud qualify as risks inherent within the organization. It is against this backdrop that this paper investigated the role of information systems in mitigating risks facing Rolls-Royce Company.
This research employed a structured survey method to collect data from participants. The data were collected through the use of structured questionnaires. The participants were selected from the organization using random sampling method. The entire company was too large to undertake a research of this nature. Consequently, the researcher used a random sampling method to select three key employees from the IT department, human resource department, administration department and accounts department. Thus, a total of 12 respondents participated in this study. These departments were selected intentionally since they are thought to be more conversant with the topic under investigation. The case study approach was used in this study to gain deep knowledge regarding the role of information system (ERP) in mitigating risks facing the selected organization. Furthermore, the current research used both primary and secondary data for to collect relevant information pertaining to the topic.
In order to collect primary data, questionnaires were sent the selected people who were in a position to provide relevant information to the study. The questionnaires were sent to personnel working in the human resource department, administration department, accounts/finance department and IT department. In addition, secondary data was collected via meticulous and extensive internet search for information pertaining to the subject at hand. The researcher used various navigators such as Google Scholar, bibsys and Google Book to search for information on key words such as information systems, risk management and names of prominent professors and scholars related to the concept. The internet search led to different articles, books, journals and other publications.
Conclusion
The current research has addressed some of the risk management processes carried out by business organizations. It has also discussed how the ERP / SAP system can benefit business firms (such as Rolls-Royce) in the risk management process. The current research conducted a thorough literature review and analysed a case study (Rolls-Royce) and concluded that information systems play an important role in the process of risk management. This research has also demonstrated that the ERP/SAP system can mitigate risks associated with the damage to the Company’s reputation, brand image and the confidence of customers regarding the precision of business processes. The current study shows that information systems (i.e. ERP/SAP) can improve supply chain systems and ensure that customer orders are processed and delivered on time.
Data security is another major risk facing manufacturing firms. Consequently, the current research has demonstrated how the Data Warehouse system can mitigate the risk of unauthorized access to confidential data. The Data Warehouse system is an integral part of the ERP/SAP system that allows only authorized personnel to access confidential data required to make sound managerial and business intelligence decisions.
The literature review and the case study findings have demonstrated that information systems can only be effective in the process of risk management if they get support and commitment from relevant stakeholders. A majority of the interviewees mentioned the need for enhancing a better understanding regarding the role of ERP/SAP in the processes of risk management. The view that individuals from different business department do not communicate well has been recognized in this study as an elementary issue that can affect the capability of the new information system in mitigating business risks facing Rolls-Royce. This finding supports the results of the study conducted by Jern (2009) regarding the significance of reciprocal communication among various business departments in ensuring that the information system facilitates the process of risk management.
The literature review and the interview findings suggest that the competence of the end users is a key element that can determine the success of an information system in mitigating business risks. Consequently, there is an urgent need to execute proper training programs as well as mechanisms of knowledge transfer to facilitate the proper functioning of the information system. A number of interviewees mentioned that the training program was too short and did not cover all the relevant aspects relating to the new information system. Therefore, the current research suggests that organizations in the healthcare sector, energy sector and manufacturing sector would benefit immensely by training their staff on how to use information systems in the process of risk management.
The process of risk management should also be perceived via a prism that inspires business organizations to exploit their intrinsic capabilities. As mentioned, earlier, organizations can use information systems to assess and monitor emerging risks, dispense resources and determine appropriate strategies for mitigating risks. What is more, the management must demonstrate the manner in which the organization’s core processes can guide other business divisions to deal with their respective vulnerabilities to destructive risks. Thus, organizations that employ information systems effectively in the process of risk management are likely to reap economic benefits as well as considerable goodwill.
Recommendations
Although many companies have put in place systems and structures to deal with risks, the current practices disclose that they have failed mainly because of the intrinsic features of these risks. It is a common practice among companies to pursue short term solutions at the expense of the long term strategies when dealing with potential or real risks. Thus, the organizational culture must underline the role of information systems (i.e. ERP/SAP) in mitigating emerging risks. In other words, organizations must adopt information systems as leverage for mitigating emerging risks. The current study recommends four key steps (see figure 2) that an organization can adopt to manage emerging risks.
Identifying Potential Risks
The management should strive to discern potential risks relative to the strategic goals of the organization. They should not only identified risks but also attempt to detect unknown risks which could be unravelled via examination of the historical information. The management must analyze fluctuations in the business environment in order to make out incidences that may have had a negative effect on the value of the stakeholders in the earlier period. The major aspects that should be taken into consideration include technological, political and business events. In addition, the management should solicit the views of non-conformists, economists and academic personalities in order to make out all potential risks. Past records show that risks occur because of limited prudence, gratification and unwillingness to confront the status quo. There are different types of risks. Thus, the management should strive to harmonize the different types of risks with the current classification structure of the organization (for instance, as part of its ERP program). The management should also delineate the tolerance levels for all the relevant risks identified. This is due to the fact that some risks are extremely harmful to the business whereas others may create an opportunity to restructure the market.
Risk Assessment and Implication to Business
Risk assessment typically takes into account the organization, shareholders and the link between risks on the basis of concrete evidence. Risk assessment demands a comprehensive analysis of the correlation between risks as well as their impacts. Organizations can employ scenario analysis to assess their vulnerability to risk exposures as well as the degree of preparedness in case a tragic threat emerges. The analysis of risk scenarios can be accomplished using a risk rating scale. For example, an organization can use quantitative rating scales to achieve a superior level of measurability and accuracy with respect to the process of risk assessment. The risk rating scales offer a uniform platform of assessment which allows the prioritization of risks as well as establishing the appropriate actions to be adopted on the basis of the organization’s risk tolerance.
Establishing Strategies for Risk Response
Risk response differs according to the company’s level of tolerance, the amount of risks the company is prepared to take and the process of risk assessment. The organization must use concrete evidence when choosing the appropriate responses to risks. For example, it many opt to acknowledge some risks on the basis of inherent counterbalances within a portfolio. However, a collaborative strategy should be adopted when the risks transcend the organization’s tolerance level. A collaborative approach seems to be the only viable option for mitigating risks and safeguarding organization’s assets.
The same approach is useful in mitigating risks among various business divisions. It deserves merit to mention that business divisions have dissimilar resources and exposure pertaining to a given risk. Thus, the management must recognize that the impact of a particular risk on one division may substantially differ from that of another division. In addition, autonomous business divisions must acknowledge the advantages of collaborating with other divisions. Whereas one business division may be vulnerable to a particular risk, another business division may be in a position to help alleviate that risk and benefit the entire organization. In a nutshell, business divisions must work together in order to mitigate emerging risks. Collaboration can assist the organization downsize the negative effects of risks and alleviate threats via sound risk management strategies.
Monitoring Risks using Key Indicators
In order to make sound decisions, organizations must regularly examine and monitor progress in their respective business environments to detect vulnerabilities to risks. This can be achieved via comprehensive assessment of the current and future trends in the market. The management should employ this information to explicate unidentified risks as well as their potential influence on the business processes. What is more, expert opinion should be solicited regarding this matter. The management should recognize the salient characteristics of a potential risk in order to select appropriate risk responses. In addition, information systems should be used to store crucial data pertaining to useful indicators in order to augment the process of risk mitigation. Key stakeholders within the organization must also be conversant with the potential risks to strategic and business objectives of the company. The organization must set aside sufficient resources and skills in order to effectively monitor key indicators on a regular basis. To be specific, the organization must:
- Relate risks to the strategic objectives of the business
- Set aside sufficient resources to facilitate analysis of emerging risks
- Employ established risk controls and indicators to analyze fluctuations in the market environment
- Improving the technical capability in order to pay attention to feeble market indicators of potential risks
- Employ relevant data in the risk management process
Although human resources are crucial with regard to the process of risk management, business organizations must set aside additional resources to augment technical capabilities of the organization in order to detect and track key indicators as well as feeble market indicators of potential risks. Business organizations must also carry out long-term studies to detect and track potential risk signals in order to mitigate the adverse effects of unidentified risks. These studies will also enable the organization to develop the dexterity to deal with undetectable risks when they materialize. Given that emerging risks are interrelated, adequate resources should be set aside to help create robust risk management strategies that can facilitate the accomplishment of strategic goals of the organization.
Suggestions for Future Research
The major objective of this dissertation is to help business organizations understand the benefits of using information systems in the process of risk management. As discussed in previous sections, this study has shown that information systems (i.e. ERP/SAP) can be effective in mitigating risks arising from unauthorized access to confidential data, human errors, unfilled customers’ orders and moribund supply chain systems. Future studies should attempt to investigate how the Passenger Reservation System (PRS) can benefit the process of risk management in a company found in the transport sector.
The main objective of this study was to investigate the role of information systems in the process of risk management in a selected organization. Consequently, the current research used Rolls-Royce as a case study to investigate the topic at hand. A comparative study should therefore be carried out in the future to assess the impact of information systems in mitigating risks apparent in different sectors of the economy. For example, future studies should compare how information systems are beneficial in the process of risk management in the health care sector and the energy sector.
References
Andrews, D & Moss, R 2002, Reliability and Risk Assessment, Professional Engineering Publishing Limited, London.
Audit Commission 1990, Preparing an information technology strategy, HMSO, London.
Axelrod, R 2003, Risk in Networked Information Systems, University of Michigan, Ann Arbor, MI.
Beasley, S, Clune, R & Hermanson, D 2005, ‘Enterprise risk management: An empirical analysis of factors associated with the extent of implementation’, Journal of Accounting and Public Policy, vol. 24, no. 6, pp. 521–531.
Berkowitz, B 2003, The New Face of War, Free Press, New York.
Beynon-Davies, P & Williams, D 2003, ‘The Diffusion of Information Systems Development Methods’, Journal of Strategic Information Systems, vol.12, no.1, pp. 29-46.
Birch, D & McEvoy, N 1992, ‘Risk analysis for information systems’, Journal of Information Technology, vol. 7 no 1, pp. 44-53.
Boehm, B 1991, ‘Software Risk Management: Principles and Practices’, IEEE Software, vol. 8, no.1, pp. 32-41.
Braithwaite, J & Drahos, P 2000, Global business regulation, Cambridge University Press, Cambridge.
Bryman, A & Bell, E 2007, Business Research Methods, 2nd edition, Oxford University Press, Oxford.
Chapman, C & Ward, S 2002, Managing project risk and uncertainty, John Wiley & Sons, Chichester, UK.
Chapman, C & Ward, S 1997, Project Risk Management: Processes, Techniques and Insights, John Wiley & Sons, Chichester, United Kingdom.
Chapman, R 1998, ‘The Effectiveness of Working Group Risk Identification and Assessment Techniques’, International Journal of Project Management, vol.16 no.6, pp. 333-343.
Chen, X, Doerpinghaus, H & Lin, X 2008, ‘Catastrophic losses and insurer profitability: evidence from 9/11’, The Journal of Risk and Insurance, vol. 75 no. 1, pp. 39-62.
Chorafas, D 2008, Risk Accounting and Risk Management for Accountants, Elsevier, United Kingdom.
Cockburn, A 2001, Crystal Clear: A human-powered software development methodology for small teams, Addison-Wesley, Reading.
Committee on National Security Systems 2006, National information assurance glossary, Ft Meade, MD, USA.
DeMarco, T & Lister T 2003, ‘Risk Management during Requirements’, IEEE Software, vol. 20 no. 5, pp. 99-101.
Figlewski, S & Levich, M 2002, Risk Management; the State of the Art, Kluwer Academic Publishers, London.
Gibson, M 1997, Information systems for risk management, Federal Reserve Board, Washington, D.C.
Grey, S 1995, Practical Risk Assessment for Project Management, John Wiley & Sons Ltd, Chichester, United Kingdom.
Haimes, Y 1998, Risk Modelling, Assessment, and Management, John Wiley & Sons, Inc, New York, USA.
Hall, M 1998, Managing Risk: Methods for Software Systems Development, Addison Wesley, Reading.
Hillson, D 2001, Extending the Risk Process to Manage Opportunities, Fourth European Project Management Conference, PMI Europe, London.
Holt, M 2006, The Sarbanes-Oxley act: overview and implementation procedures, Elsevier CIMA Publication, Oxford.
IFA 1999, Enhancing shareholder wealth by better managing business risk, IFA, New York.
IRM 2002, IRM 2002, A risk management standard, The Association of Insurance and Risk Managers, London.
Jern, A 2009, On Introducing Information Systems in Organizations, Helsinki University of Technology, Helsinki.
Jorion, P 2001, Value at Risk, the new benchmark for managing financial risk, McGraw-Hill, London, UK.
Klinke, A & Renn, O 2002, ‘A New Approach to Risk Evaluation and Management: Risk-Based, Precaution-Based, and Discourse-Based Strategies’, Risk Analysis, vol. 22, no. 6, pp. 1071-1094.
Kunreuther, H 2002, ‘Risk analysis and risk management in an uncertain world’, Risk Analysis, no. 22 no.4, pp. 655-664.
Lawrence, D 1995, Aggregating credit exposures: The simulation approach, Risk Publications, London.
Loh, T & Koh, S 2004, ‘Critical elements for a successful enterprise resource planning implementation in small-and medium-sized enterprises’, International Journal of Production Research, vol. 42 no. 17, pp. 3433-55.
Mabert, V, Soni, A & Venkataramanan, M 2003, ‘Enterprise resource planning: managing the implementation process’, European Journal of Operational Research, vol. 146 no. 2, pp. 302-14.
Mandal, P & Gunasekaran, A 2003, ‘Issues in implementing ERP: a case study’, European Journal of Operational Research, vol. 146 no. 2, pp. 274-83.
Maurer, A 2008, ‘Optimization Alternatives of Information Systems for Risk Management’, Revista Informatica Economica, vol. 3 no. 47, pp. 28-33.
McAfee, A 2002, ‘The impact of enterprise technology adoption on operational performance: an empirical investigation’, Production and Operations Management, vol. 11 no. 1, pp. 33-53.
Melnikov, A 2004, Risk Analysis in Finance and Insurance, Translated and edited by Alexei Filinkov. Chapman & Hall/CRC Monographs and Surveys in Pure and Applied Mathematics, London.
Nacco, B & Stulz, R 2006, ‘Enterprise Risk Management – theory and practice’, Journal of Applied Corporate Finance, vol. 18 no. 4, pp. 8-20.
Nah, F & Delgado, S 2006, ‘Critical success factors for enterprise resource planning implementation and upgrade’, Journal of Computer Information Systems, vol. 46 No. 5, pp. 99-113.
Nickerson, R 2000, Business and information systems, Prentice Hall, London.
Picoult, E 1996, Measuring pre-settlement credit risk on a portfolio basis, Proceedings of a Joint Central Bank Research Conference.
Porthin, M 2004, Advanced case studies in risk management, Helsinki University of Technology, Helsinki.
Reifer, D 2002, ‘How good are agile methods?’, IEEE Software, vol.19 no. 4, pp.16-18.
SANS 2006, An introduction to information system risk management, Web.
Scapens, R 1990, ‘Researching Management Accounting Practice: The role of Case Study Methods’, The British Accounting Review, vol. 22, pp. 259-281.
Schneier, B 2000, Secrets and Lies: Digital Security in a Networked World, Wiley, New York.
Schwalbe, K 2000, Information Technology Project Management, Course Technology, Thomson Learning, London.
Smith, P & Merritt, G 2002, Proactive Risk Management: Controlling Uncertainty in Product Development, Productivity Press, Manchester.
Stapleton, J 1997, DSDM: Dynamic Systems Development Method, Addison Wesley, Harlow, England.
Stulz, M 1996, ‘Rethinking risk management’, Journal of Applied Corporate Finance, vol. 9 no. 3, pp. 8-24.
Wiegers, K E 1998, ‘Know Your Enemy: Software Risk Management’, Software Development, vol. 6, no.10, pp. 38-42.
Williams, L & Cockburn A 2003, ‘Agile Software Development: It’s about Feedback and Change’, IEEE Computer Society, vol. 36 no. 6, pp. 39-43.
Williams, R & Walker, A 1997, ‘Putting Risk Management into Practice’, IEEE Software, vol. 14 no. 3, pp. 75-81.
Wiseman, D 1992, ‘Information economics: A practical approach to valuing information systems’, Journal of Information Technology, vol. 7 no. 3, pp. 169-179.
Wognum, P, Krabbendam, J, Buhl, H, Ma, X & Kenett, R 2004, ‘Improving enterprise system support-a case-based approach’, Advanced Engineering Informatics, vol.18, no. 4, pp. 241.
Yusuf, Y, Gunasekaran, A & Abthorpe, M 2004, ‘Enterprise information systems project implementation: A case study of ERP in Rolls-Royce’, Int. J. Production Economics, vol. 87, pp. 251–266.
APPENDIX
Questionnaire
This is a master’s research work that aims to investigate how information systems can benefit the process of risk management. Any information given will be kept confidential. Thank you for your participation.
Part One
Background Information
- Educational background………………………………………..
- Name of the Company……………………………………………
- Division………………………………………………………………..
- Position held…………………………………………………………
Part Two
Risk Management
- Effective risk management plays an important role to the attainment of your organization’s goals
- Strongly agree
- Agree
- Neutral
- Disagree
- Strongly disagree
- The performance of your organization can be improved via effective risk management
- Strongly agree
- Agree
- Neutral
- Disagree
- Strongly disagree
- The responsibility for risk management is well documented within your organization.
- Strongly agree
- Agree
- Neutral
- Disagree
- Strongly disagree
- Appropriate resources are allocated by your organization to support risk management process.
- Strongly agree
- Agree
- Neutral
- Disagree
- Strongly disagree
- Sufficient resources are provided by your organization to carry out relevant staff training to develop their skills in risk management.
- Strongly agree
- Agree
- Neutral
- Disagree
- Strongly disagree
Part Three
Information Systems
- Does your organization use an information system to report company transactions in accordance with the established guidelines?
- yes
- no
- Does your organization’s information systems capable to detect risks facing the company?
- Yes
- No
- Are all employees in your organization conversant with workings of the information system?
- Yes
- No
- Does the new information system enable the management to make sound decisions relating to the business processes of the organization?
- Yes
- No
Part Four
General Questions
- What does risk management process mean to you?
- Are you aware of any risks facing your organization? If yes, what risk management strategies have been put in place to address this problem?
- Estimate the acceptance rate of the ERP/SAP system in your organization:
- very accepted
- accepted
- moderately accepted
- not accepted
- In your opinion, what are the three key success factors when deploying an information system?
- In your opinion, do you think the ERP/SAP system will benefit the process of risk management in your organization?
- strongly agree
- agree
- disagree
- strongly disagree
- State and describe one or a few areas of the organization that will benefit from Is deployment
- Mention some of the risks that will be mitigated by the new information system
- In your opinion, do you think proper training program was provided on how to use the new information system?